VULNERABILITY ASSESSMENTS
For your IT infrastructure
IDENTIFY.
ANALYZE.
QUANTIFY.
MITIGATE.

Four types of vulnerability assessments.
- Host – looks at critical servers and workstations.
- Network and Wireless – discover unauthorized access of devices or unknown users.
- Database assessments – discovery of misconfigurations, rogue databases or insecure dev/test environments, etc.
- Application scans – website applications and their source code.
The 4-step security scanning process:
- Vulnerability Identification (testing) -Simply put, this step provides a comprehensive list of an application’s vulnerabilities.
- Analysis – to identify the source and root cause of items in step one.
- The Risk Assessment – prioritizes the vulnerabilities by assigning a severity score.
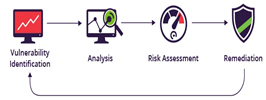
- Remediation – the closing of any security gaps identified.

Vulnerability assessments determine your systems susceptibilities to any known threats or vulnerabilities
QUICKLY UNDERSTAND ANY
REMEDIATION OR MITIGATIONS NECESSARY
To better secure your business.

BENEFITS:
- Validate effectiveness and health of current security safeguards, system updates, and upgrades
- Understand the risk level of your IT infrastructure and corrective actions needed to improve security posture
- Provides clear, actionable information on any identified threats before hackers find them
- Quantifiable value of risks
- Improves security and resource allocation buy in from stakeholders

Does Your Organization need a Vulnerability Assessment?
- Validate effectiveness and health of current security safeguards, system updates, and upgrades
- Understand the risk level of your IT infrastructure and corrective actions needed to improve security posture
- Provides clear, actionable information on any identified threats before hackers find them
- Quantifiable value of risks
- Improves security and resource allocation buy in from stakeholders